Red Team Assessment in Corporate Situations
Every company is an attractive target for skilled attackers – including yours. Whether it’s customer, payment, communication or health data, manufacturing plans, research and development results, formulas, utility networks such as water and electricity, or simply your money, every company has assets that are worth stealing or sabotaging. The numbers confirm this: 44% of all German companies have been the victim of an espionage attack in the last three years [source: www.reuters.com ], although the number of unreported cases is probably much higher. This is where Red Teaming comes in!
A Red Team Assessment provides a realistic analysis of how vulnerable your company really is to actions by professional groups that have targeted your company. NSIDE identifies strategies and ways that hackers can target, infiltrate, and steal your most sensitive data and sabotage your most critical systems. Our analysis lets you identify these efficient and effective pathways for intruders, close them down, and thus systematically improve your security. A Red Teaming Assessment allows you to fully test the security of your organization as a whole.
Red Team Exercises (also known as Red Team Assessments or Red Team Engagements) are full-scale attack simulations or ‘Adversary Simulations’. In them, an experienced team (the Red Team) assumes the attacker position and subjects a target organization to a practical test by a hacker attack using all the latest attack techniques. Since it is often mainly targeted attacks that are well prepared or executed over a longer period of time – what are known as Advanced Persistent Threats or APTs – that are simulated, they are sometimes also referred to as APT simulations.
At the same time, this tests your defensive capabilities: Does your security team detect the hallmarks of a serious attack? If so, how quickly? Or can attackers pentrate your systems, infiltrating and accessing your most sensitive trade secrets without you noticing?
For this, NSIDE, which has specialized in Red Teaming Assessments since its inception, employs the same techniques as real cyberattacks: social engineering, physical incursions, malware engineered for the specific application or developed from scratch, lateral movement techniques to spread between internal systems, bypassing techniques to get around firewalls and virus scanners, persistence and stealth techniques known from APTs, and many more.
Since Red Team Assessments are designed to simulate attacks as realistically as possible, they are based on the phases of attacks classically seen in cyberattacks. These phases are also called the ‘cyber kill chain’.
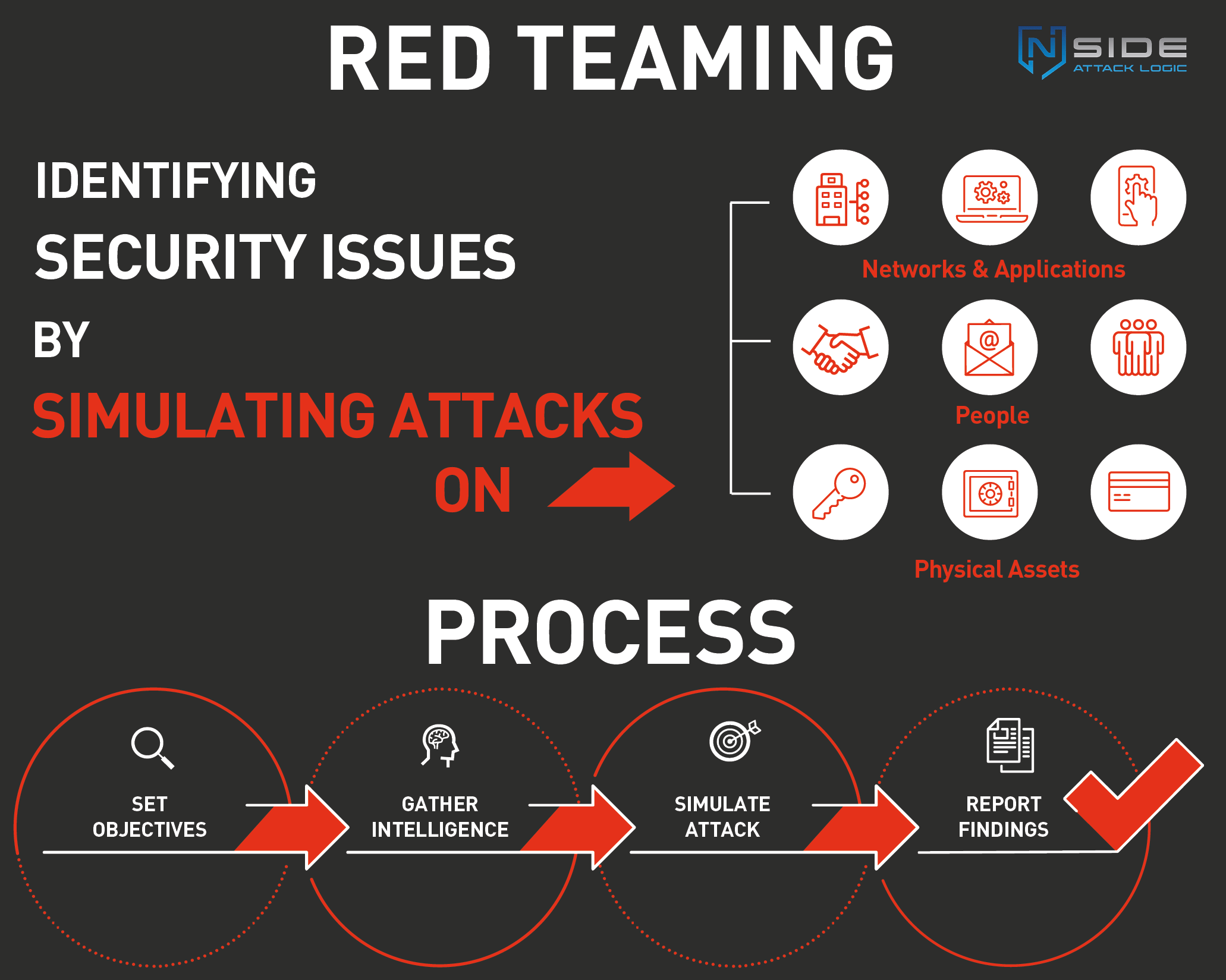
Phases of Red Team Assessment
How do Red Teaming and Penetration Testing differ?
The test object of a Red Team Assessment is always an organization or organizational unit, whereas the test object of penetration testing is a technical development or environment. Red Team Assessments are also usually goal and statement driven: How can an intruder get to my ‘most valuable assets’ (Critical Assets) or compromise sensitive systems and business units (Critical Functions)? How good is my organization’s Cyber Resilience and Posture? In other words, how well can my team and its tools detect, block, and contain such attacks? What do my processes look like?
Pentests, on the other hand, are focused on detecting technical vulnerabilities. They try to disclose them as fully as possible, while Red Team Assessments act like aggressors and focus only on those vulnerabilities that would allow the intruder to reach his target – but in the area of technology, people and processes/organization.
The following table illustrates the differences between penetration testing and red teaming:

RED TEAM EXCERCISE
Test object:
Organization or organizational unit
Dimensions:
Holistic: Technical, human, organizational.
Perspective focus:
Strategic and tactical, as well as technically and operationally in part.
Test objective:
To answer the question: “Can aggressors gain access to my ‘most valuable resources’ (Critical Assets) or gain control of my most important systems or business processes (Critical Functions)?” If so, how? What are my detection measures and countermeasures?
Statements and questions:
How secure is my organization as a whole? What gateways do I have that help attackers gain Critical Assets and Critical Functions? How good are my response processes? How well can I proactively block attacks? How well can I detect and respond to attacks?
Knowledge gain:
What are my organization’s key technical, human, and organizational/process vulnerabilities? How well is my defense set up? What are the risks to my business as a whole?
Completeness:
Key vulnerabilities of the organization in the area of technology, processes/organization, and people.
Recommendations and results:
Eliminate blind spots in detection, address vulnerabilities in the three dimensions (technical/process/organizational/human), strengthen response to attacks against the organization, improve proactive and preventive measures for corporate security, strengthen general defenses against attacks (cyber resilience and posture), improve processes, provide direction for security strategy, risk assessment
Attacker model:
Professional human aggressors with malicious intent against my own organization
Insiders on Client Side:
Only one or two key people, no one else

PENETRATION TEST
Test object:
Technical systems, applications, environments, infrastructures.
Dimensions:
Technical
Perspective focus:
Technical-operational, in part strategic and tactical.
Test objective:
To detect as many technical vulnerabilities as possible
Statements and questions:
How secure is the test object and what vulnerabilities exist
Knowlege gain:
What are my organization’s key technical, human, organizational/process vulnerabilities? How well is my defense set up? What are the risks to my business as a whole? What are the risks to the test object, the data stored on it, and their users? What exactly are the security vulnerabilities and how can I fix them?
Completeness:
As complete as possible, uncovering as many technical vulnerabilities in the test object as possible.
Recommendations and results:
Securing the test object against hacker attacks and technical risks, recommendations and guidance on how to fix the vulnerabilities.
Attacker model:
Any attacker
Insiders on client side:
Project and system managers, no special restrictions.

